Late in the day one may have encountered many application asking for Second Factor authentication. Most of those uses OTP (One Time Password) via email or SMS. However we have new competitor in this arena, called TOTP (Time Based OTP) apps. There are many big players are in the race, i.e Google Authenticator and Microsoft Authenticator App

There are many methods employed for 2FA, like OTP (via SMS and email), dedicated app or using third party apps.
If you turn on two-step verification for your account, then each time you log in on a new computer you’ll need to complete an extra step of verification in addition to supplying your normal password.
By completing this extra step it proves that you possess something that would be hard for an attacker to get hold of: either a dedicated security device, or a secret code held securely in an app on your mobile phone.
Note: When you log in, you can choose to trust that computer, so you won’t need to do the second step again every time you log in.
How TOTP (authenticator apps) work
TOTP stands for Time-Based One-Time Password. It is a standardised method for generating a regularly changing code based on a shared secret (that is to say, shared by our server and your phone; no one else!). Because it’s a standard, you can get many different (and mostly free) authenticator apps for your mobile phone that support it. Some of the most popular ones are Google Authenticator, Authy, Duo and 1Password.

When you set up TOTP, application server generates a secret key - a bunch of random numbers and letters. You then save this key to your phone, normally by scanning a QR code (2D bar code) with your authenticator app. (If your phone doesn’t have a camera, you can manually type in the long code instead.)
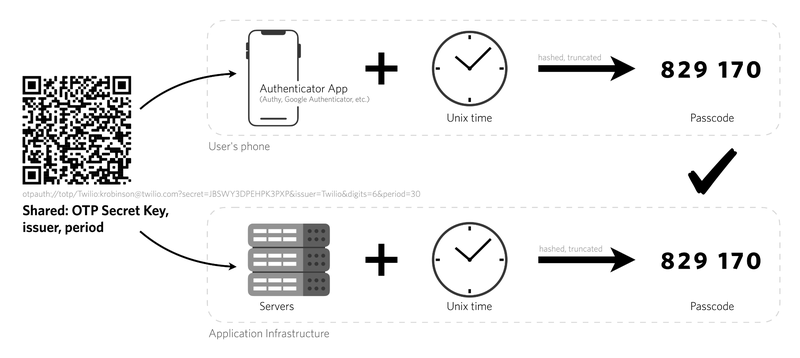
Now your phone and our server both have a copy of this secret key. When you want to log in, you need to prove that you have the key. To do this, your app combines the key with the current time (to the nearest 30 seconds) to produce an access code. It does this using something called a “secure hash function” (for the crypto-heads out there, it uses HMAC-SHA-1, just so you know). In layman’s terms, it mixes the time and your key together to produce an output that’s unique (if the time or the key are different in even the slightest way then the output is completely different), but impossible to reverse (knowing the output doesn’t help you guess the secret key). To make it easier to type, the access code is shortened to a 6-digit number.
When prompted, you type the code into the input box:
Application server repeats the process and if the code matches, you’re in!
Strengths and weaknesses
With free apps available for iPhone, Android, Blackberry and even Windows Phone, TOTP is a quick, cheap and easy way to enable two-step verification. It’s the most widely supported method too – you can use the same app to secure your accounts at Google, Dropbox, GitHub and many more.
The way it works is simple (in crypto terms) and secure. Even if an attacker sees a one-time code, there’s absolutely no way for them to guess what the next one will be. The only way you can do that is with the secret key, which stays safely on your phone and our server.
Because the access code is generated from the current time, your phone and our server have to be roughly in agreement about what time it is for the process to work. This is rarely an issue though since all phones keep their clocks in sync using the internet (and don’t worry, time zones are ignored!, UTC time is used always).
The code generated is valid for about 60 seconds (to allow for clock skew), so in theory if someone intercepts both the access code and your password they have a short window of time where they could use it (a replay attack).
There is no protection in TOTP against an attacker tricking you into typing the code in duplicate website (a phishing attack). Remember it’s easy to check you’re on the real website before typing in your credentials (like you should be doing before entering password).
Since the secret key is on your phone, not a dedicated security device, should you get malware on the phone it may be able to steal the secret key. This is still a much harder proposition for an attacker than not having any two-step verification to get past though!
Got any security questions or recommendations? Tweet us @bagwanpankaj using the hashtag #securityquestions.
About The Author
I am Pankaj Baagwan, a System Design Architect. A Computer Scientist by heart, process enthusiast, and open source author/contributor/writer. Advocates Karma. Love working with cutting edge, fascinating, open source technologies.
To consult Pankaj Bagwan on System Design, Cyber Security and Application Development, SEO and SMO, please reach out at me[at]bagwanpankaj[dot]com
For promotion/advertisement of your services and products on this blog, please reach out at me[at]bagwanpankaj[dot]com
Stay tuned <3. Signing off for RAAM
